On each of those applications that says 'read and review the following policies' it is important to do that even should it only be a 'trail offer' as in most cases the iphone is of a contact to the contract and all the information of you and store is now on the stream.
Showtime is only an example as I have DISH Television and do not suffer these product infringements in my life. For I order through DISH and that is and has been my path to how I have always watched television where cable is unavailable. Even at that understanding it is the further comprehension that I bought my Roku at Target which makes the product registry with the original box and instructions thereof. That is why the retail stores are in the fashion of knowing how important it is not to just stream-live edition of product but to enjoy the shelves as the stock is of all sew. This makes the safety to my home in total as there is no-way to path a counter to hacking any account should I have established both DISH and Roku for the regular scheduled programs, pay-per-view and the Movie Channels.
Please follow the instructions of your recommended reads or the fathom of your sell will identify your lie as agreed upon by only one click to try something out!!
It is the http: that is being lost on the web and that // to the www is also beginning to reserve itself to the type that seems to not show up on the tool bar. These are the basic call sites that identify the Internet to the Worldwide Web and insure that the site you are approving application to is in the staff of the client privileged file and not the face of anonymous trending. Be wise not an assumption as the hacking reported today is as easily identified as attempting to read these contracts is to the length of time it takes to type the correct addy and not the shortened stripped down version of the i.p. address.
Terms of Use for streaming Showtime
http://www.showtime.com#termsAndconditions
Privacy Policy for streaming Showtime
http://www.showtime.com#privacy
Video Services Policy for streaming Showtime
http://www.showtime.com#videoServicesPolicy
The actual I.P. Address is extremely important in order to read the correct site for the correct trending of the show that you have chosen to download. Remember the words change as fast as the Con comes to the Times of the multiplication of money versus public awareness.
1. Terms of Use | SHOWTIME
www.sho.com/about/terms
Showtime
For example, special provisions applicable to the Showtime standalone streaming service (the "Streaming Service") are contained in Section 8, and special ...
2. https://en.wikipedia.org/wiki/Section_8_(military)
3. https://en.wikipedia.org/wiki/Section_8_(housing)
4. https://www.mixcloud.com/discover/section-8/
5. http://www.fandango.com/section8_95371/criticreviews
6. https://www.hiphop.melbourne/events/out-to-play-section-8

IP address
From Wikipedia, the free encyclopedia
An Internet Protocol address (IP address) is a numerical label assigned to each device (e.g., computer, printer) participating in a computer network that uses the Internet Protocol for communication.[1] An IP address serves two principal functions: host or network interface identification and location addressing. Its role has been characterized as follows: "A name indicates what we seek. An address indicates where it is. A route indicates how to get there."[2]
The designers of the Internet Protocol defined an IP address as a 32-bit number[1] and this system, known as Internet Protocol Version 4 (IPv4), is still in use today. However, because of the growth of the Internet and the predicted depletion of available addresses, a new version of IP (IPv6), using 128 bits for the address, was developed in 1995.[3]IPv6 was standardized as RFC 2460 in 1998,[4] and its deployment has been ongoing since the mid-2000s.
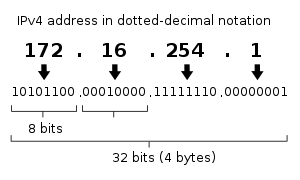
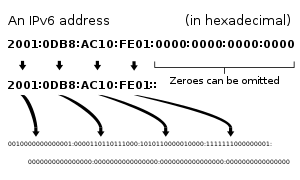
IP addresses are usually written and displayed in human-readable notations, such as 172.16.254.1 (IPv4), and 2001:db8:0:1234:0:567:8:1 (IPv6).
The Internet Assigned Numbers Authority (IANA) manages the IP address space allocations globally and delegates five regional Internet registries (RIRs) to allocate IP address blocks to local Internet registries (Internet service providers) and other entities.
Contents
[hide]IP versions
Two versions of the Internet Protocol (IP) are in use: IP Version 4 and IP Version 6. Each version defines an IP address differently. Because of its prevalence, the generic term IP address typically still refers to the addresses defined by IPv4. The gap in version sequence between IPv4 and IPv6 resulted from the assignment of number 5 to the experimentalInternet Stream Protocol in 1979, which however was never referred to as IPv5.
IPv4 addresses
Main article: IPv4 § Addressing
In IPv4 an address consists of 32 bits which limits the address space to 4294967296 (232) possible unique addresses. IPv4 reserves some addresses for special purposes such as private networks (~18 million addresses) or multicast addresses(~270 million addresses).
IPv4 addresses are canonically represented in dot-decimal notation, which consists of four decimal numbers, each ranging from 0 to 255, separated by dots, e.g., 172.16.254.1. Each part represents a group of 8 bits (octet) of the address. In some cases of technical writing, IPv4 addresses may be presented in various hexadecimal, octal, or binary representations.
Subnetting
In the early stages of development of the Internet Protocol,[1] network administrators interpreted an IP address in two parts: network number portion and host number portion. The highest order octet (most significant eight bits) in an address was designated as the network number and the remaining bits were called the rest field or host identifier and were used for host numbering within a network.
This early method soon proved inadequate as additional networks developed that were independent of the existing networks already designated by a network number. In 1981, the Internet addressing specification was revised with the introduction of classful network architecture.[2]
Classful network design allowed for a larger number of individual network assignments and fine-grained subnetwork design. The first three bits of the most significant octet of an IP address were defined as the class of the address. Three classes (A, B, and C) were defined for universal unicast addressing. Depending on the class derived, the network identification was based on octet boundary segments of the entire address. Each class used successively additional octets in the network identifier, thus reducing the possible number of hosts in the higher order classes (B and C). The following table gives an overview of this now obsolete system.
| Class | Leading bits | Size of network number bit field | Size of rest bit field | Number of networks | Addresses per network | Start address | End address |
|---|---|---|---|---|---|---|---|
| A | 0 | 8 | 24 | 128 (27) | 16,777,216 (224) | 0.0.0.0 | 127.255.255.255 |
| B | 10 | 16 | 16 | 16,384 (214) | 65,536 (216) | 128.0.0.0 | 191.255.255.255 |
| C | 110 | 24 | 8 | 2,097,152 (221) | 256 (28) | 192.0.0.0 | 223.255.255.255 |
Classful network design served its purpose in the startup stage of the Internet, but it lacked scalability in the face of the rapid expansion of the network in the 1990s. The class system of the address space was replaced with Classless Inter-Domain Routing (CIDR) in 1993. CIDR is based on variable-length subnet masking (VLSM) to allow allocation and routing based on arbitrary-length prefixes.
Today, remnants of classful network concepts function only in a limited scope as the default configuration parameters of some network software and hardware components (e.g. netmask), and in the technical jargon used in network administrators' discussions.
Private addresses
Early network design, when global end-to-end connectivity was envisioned for communications with all Internet hosts, intended that IP addresses be uniquely assigned to a particular computer or device. However, it was found that this was not always necessary as private networks developed and public address space needed to be conserved.
Computers not connected to the Internet, such as factory machines that communicate only with each other via TCP/IP, need not have globally unique IP addresses. Three non-overlapping ranges of IPv4 addresses for private networks were reserved in RFC 1918. These addresses are not routed on the Internet and thus their use need not be coordinated with an IP address registry.
Today, when needed, such private networks typically connect to the Internet through network address translation (NAT).
| Start | End | No. of addresses | |
|---|---|---|---|
| 24-bit block (/8 prefix, 1 × A) | 10.0.0.0 | 10.255.255.255 | 16777216 |
| 20-bit block (/12 prefix, 16 × B) | 172.16.0.0 | 172.31.255.255 | 1048576 |
| 16-bit block (/16 prefix, 256 × C) | 192.168.0.0 | 192.168.255.255 | 65536 |
Any user may use any of the reserved blocks. Typically, a network administrator will divide a block into subnets; for example, many home routers automatically use a default address range of 192.168.0.0 through 192.168.0.255 (192.168.0.0/24).
IPv4 address exhaustion
Main article: IPv4 address exhaustion
High levels of demand have decreased the supply of unallocated Internet Protocol Version 4 (IPv4) addresses available for assignment to Internet service providers and end user organizations since the 1980s. This development is referred to as IPv4 address exhaustion. IANA's primary address pool was exhausted on 3 February 2011, when the last five blocks were allocated to the five RIRs.[5][6] APNIC was the first RIR to exhaust its regional pool on 15 April 2011, except for a small amount of address space reserved for the transition to IPv6, intended to be allocated in a restricted process.[7]
IPv6 addresses
Main article: IPv6 address
The rapid exhaustion of IPv4 address space prompted the Internet Engineering Task Force (IETF) to explore new technologies to expand the addressing capability in the Internet. The permanent solution was deemed to be a redesign of the Internet Protocol itself. This new generation of the Internet Protocol was eventually named Internet Protocol Version 6 (IPv6) in 1995.[3][4] The address size was increased from 32 to 128 bits (16 octets), thus providing up to 2128 (approximately3.403×1038) addresses. This is deemed sufficient for the foreseeable future.
The intent of the new design was not to provide just a sufficient quantity of addresses, but also redesign routing in the Internet by more efficient aggregation of subnetwork routing prefixes. This resulted in slower growth of routing tables in routers. The smallest possible individual allocation is a subnet for 264 hosts, which is the square of the size of the entire IPv4 Internet. At these levels, actual address utilization rates will be small on any IPv6 network segment. The new design also provides the opportunity to separate the addressing infrastructure of a network segment, i.e. the local administration of the segment's available space, from the addressing prefix used to route traffic to and from external networks. IPv6 has facilities that automatically change the routing prefix of entire networks, should the global connectivity or the routing policy change, without requiring internal redesign or manual renumbering.
The large number of IPv6 addresses allows large blocks to be assigned for specific purposes and, where appropriate, to be aggregated for efficient routing. With a large address space, there is no need to have complex address conservation methods as used in CIDR.
All modern desktop and enterprise server operating systems include native support for the IPv6 protocol, but it is not yet widely deployed in other devices, such as residential networking routers, voice over IP (VoIP) and multimedia equipment, and network peripherals.
Private addresses
Just as IPv4 reserves addresses for private networks, blocks of addresses are set aside in IPv6. In IPv6, these are referred to as unique local addresses (ULA). RFC 4193reserves the routing prefix fc00::/7 for this block which is divided into two /8 blocks with different implied policies. The addresses include a 40-bit pseudorandom number that minimizes the risk of address collisions if sites merge or packets are misrouted.[8]
Early practices used a different block for this purpose (fec0::), dubbed site-local addresses.[9] However, the definition of what constituted sites remained unclear and the poorly defined addressing policy created ambiguities for routing. This address type was abandoned and must not be used in new systems.[10]
Addresses starting with fe80:, called link-local addresses, are assigned to interfaces for communication on the attached link. The addresses are automatically generated by the operating system for each network interface. This provides instant and automatic communication between all IPv6 host on a link. This feature is required in the lower layers of IPv6 network administration, such as for the Neighbor Discovery Protocol.
Private address prefixes may not be routed on the public Internet.
IP subnetworks
IP networks may be divided into subnetworks in both IPv4 and IPv6. For this purpose, an IP address is logically recognized as consisting of two parts: the network prefix and thehost identifier, or interface identifier (IPv6). The subnet mask or the CIDR prefix determines how the IP address is divided into network and host parts.
The term subnet mask is only used within IPv4. Both IP versions however use the CIDR concept and notation. In this, the IP address is followed by a slash and the number (in decimal) of bits used for the network part, also called the routing prefix. For example, an IPv4 address and its subnet mask may be 192.0.2.1 and 255.255.255.0, respectively. The CIDR notation for the same IP address and subnet is 192.0.2.1/24, because the first 24 bits of the IP address indicate the network and subnet.
IP address assignment
Internet Protocol addresses are assigned to a host either anew at the time of booting, or permanently by fixed configuration of its hardware or software. Persistent configuration is also known as using a static IP address. In contrast, in situations when the computer's IP address is assigned newly each time, this is known as using a dynamic IP address.
Methods
Static IP addresses are manually assigned to a computer by an administrator. The exact procedure varies according to platform. This contrasts with dynamic IP addresses, which are assigned either by the computer interface or host software itself, as in Zeroconf, or assigned by a server using Dynamic Host Configuration Protocol (DHCP). Even though IP addresses assigned using DHCP may stay the same for long periods of time, they can generally change. In some cases, a network administrator may implement dynamically assigned static IP addresses. In this case, a DHCP server is used, but it is specifically configured to always assign the same IP address to a particular computer. This allows static IP addresses to be configured centrally, without having to specifically configure each computer on the network in a manual procedure.
In the absence or failure of static or stateful (DHCP) address configurations, an operating system may assign an IP address to a network interface using state-less auto-configuration methods, such as Zeroconf.
Uses of dynamic address assignment
IP addresses are most frequently assigned dynamically on LANs and broadband networks by the Dynamic Host Configuration Protocol (DHCP). They are used because it avoids the administrative burden of assigning specific static addresses to each device on a network. It also allows many devices to share limited address space on a network if only some of them will be online at a particular time. In most current desktop operating systems, dynamic IP configuration is enabled by default so that a user does not need to manually enter any settings to connect to a network with a DHCP server. DHCP is not the only technology used to assign IP addresses dynamically. Dialup and some broadband networks use dynamic address features of the Point-to-Point Protocol.
Sticky dynamic IP address
A sticky dynamic IP address is an informal term used by cable and DSL Internet access subscribers to describe a dynamically assigned IP address which seldom changes. The addresses are usually assigned with DHCP. Since the modems are usually powered on for extended periods of time, the address leases are usually set to long periods and simply renewed. If a modem is turned off and powered up again before the next expiration of the address lease, it will most likely receive the same IP address.
Address autoconfiguration
RFC 3330 defines an address block, 169.254.0.0/16, for the special use in link-local addressing for IPv4 networks. In IPv6, every interface, whether using static or dynamic address assignments, also receives a local-link address automatically in the block fe80::/10.
These addresses are only valid on the link, such as a local network segment or point-to-point connection, that a host is connected to. These addresses are not routable and like private addresses cannot be the source or destination of packets traversing the Internet.
When the link-local IPv4 address block was reserved, no standards existed for mechanisms of address autoconfiguration. Filling the void, Microsoft created an implementation that is called Automatic Private IP Addressing (APIPA). APIPA has been deployed on millions of machines and has, thus, become a de facto standard in the industry. In RFC 3927, the IETF defined a formal standard for this functionality, entitled Dynamic Configuration of IPv4 Link-Local Addresses.
Uses of static addressing
Some infrastructure situations have to use static addressing, such as when finding the Domain Name System (DNS) host that will translate domain names to IP addresses. Static addresses are also convenient, but not absolutely necessary, to locate servers inside an enterprise. An address obtained from a DNS server comes with a time to live, or caching time, after which it should be looked up to confirm that it has not changed. Even static IP addresses do change as a result of network administration (RFC 2072).
Conflict
An IP address conflict occurs when two devices on the same local physical or wireless network claim to have the same IP address – that is, they conflict with each other. Since only one of the devices is supposed to be on the network at a time, the second one to arrive will generally stop the IP functionality of one or both of the devices. In many cases with modern Operating Systems, the Operating System will notify the user of one of the devices that there is an IP address conflict (displaying the symptom error message[11][12]) and then either stop functioning on the network or function very badly on the network, and the user will then be stumped as to how to resolve the conflict, probably considering the situation an emergency. In some unfortunate cases, both devices will function very badly on the network. In severe cases in which one of the devices is the gateway, the network will be crippled. Since IP addresses are assigned by multiple people and systems in multiple ways, any of them can be at fault.[13][14][15][16][17]
Routing
IP addresses are classified into several classes of operational characteristics: unicast, multicast, anycast and broadcast addressing.
Unicast addressing
The most common concept of an IP address is in unicast addressing, available in both IPv4 and IPv6. It normally refers to a single sender or a single receiver, and can be used for both sending and receiving. Usually, a unicast address is associated with a single device or host, but a device or host may have more than one unicast address. Some individual PCs have several distinct unicast addresses, each for its own distinct purpose. Sending the same data to multiple unicast addresses requires the sender to send all the data many times over, once for each recipient.
Broadcast addressing
Main article: Broadcasting (computing)
In IPv4 it is possible to send data to all possible destinations ("all-hosts broadcast"), which permits the sender to send the data only once, and all receivers receive a copy of it. In the IPv4 protocol, the address 255.255.255.255 is used for local broadcast. In addition, a directed (limited) broadcast can be made by combining the network prefix with a host suffix composed entirely of binary 1s. For example, the destination address used for a directed broadcast to devices on the 192.0.2.0/24 network is 192.0.2.255. IPv6 does not implement broadcast addressing and replaces it with multicast to the specially-defined all-nodes multicast address.
Multicast addressing
A multicast address is associated with a group of interested receivers. In IPv4, addresses 224.0.0.0 through 239.255.255.255 (the former Class D addresses) are designated as multicast addresses.[18] IPv6 uses the address block with the prefix ff00::/8 for multicast applications. In either case, the sender sends a single datagram from its unicast address to the multicast group address and the intermediary routers take care of making copies and sending them to all receivers that have joined the corresponding multicast group.
Anycast addressing
Like broadcast and multicast, anycast is a one-to-many routing topology. However, the data stream is not transmitted to all receivers, just the one which the router decides is logically closest in the network. Anycast address is an inherent feature of only IPv6. In IPv4, anycast addressing implementations typically operate using the shortest-path metric of BGP routing and do not take into account congestion or other attributes of the path. Anycast methods are useful for global load balancing and are commonly used in distributedDNS systems.
Public address
A public IP address, in common parlance, is a globally routable unicast IP address, meaning that the address is not an address reserved for use in private networks, such as those reserved by RFC 1918, or the various IPv6 address formats of local scope or site-local scope, for example for link-local addressing. Public IP addresses may be used for communication between hosts on the global Internet.
Modifications to IP addressing
IP blocking and firewalls
Firewalls perform Internet Protocol blocking to protect networks from unauthorized access. They are common on today's Internet. They control access to networks based on the IP address of a client computer. Whether using a blacklist or a whitelist, the IP ad........read more at https://en.wikipedia.org/wiki/IP_address

No comments:
Post a Comment